Scalable Automation for IoT CyberSecurity Compliance: Ontology-Driven Reasoning for Real-Time Assessment
Abstract
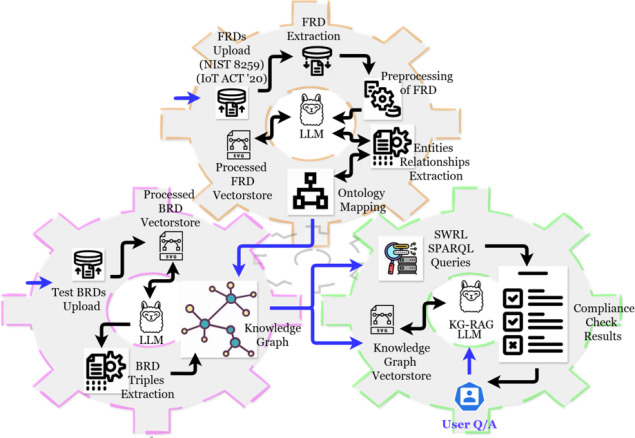
In recent years, the rapid expansion of the Internet of Things (IoT) has introduced significant cybersecurity challenges, requiring manufacturers to comply with various regulatory frameworks and cybersecurity standards. Hence, to protect user data and privacy, all organizations providing IoT devices must adhere to complex guidelines such as the National Institute of Standards and Technology Inter-Agency Report (NISTIR) 8259, which defines essential cybersecurity guidelines for IoT manufacturers. However, interpreting and applying these rules from these guidelines remains a significant challenge for companies. Previously, our Automated Knowledge Framework for IoT Cybersecurity Compliance, leveraged SWRL, SPARQL queries, Web Ontology Language and Visualization (OWL Viz), Semantic Web technologies, Large Language Models (LLMs), and Retrieval Augmented Generation (RAG) pipeline to automate compliance assessment of multiple Functional requirement documents (FRDs), while systematically cross-checking Business requirement documents (BRDs) against them Oranekwu et al. (2024). However, these efforts primarily focused on mapping NISTIR 8259 guidelines into a structured ontology laying the foundation for us to build, expand on, and then integrate the IoT Cybersecurity Improvement Act of 2020 into the compliance framework. Furthermore, exploring its big data capability, the Knowledge Graph (KG) has been expanded and populated with more than 800 manufacturer privacy policy instances, allowing direct comparison between manufacturer-defined data properties, object properties, and regulatory compliance expectations. The primary objective is to evaluate the effectiveness of this enhanced version of the framework in identifying policy non-compliance by comparing triples extracted from privacy policies against the structured knowledge representation. Through this approach, our goal is to automate compliance verification by examining the relationships between manufacturers, security requirements, and regulatory obligations, offering a scalable solution for the security governance of IoT.